- The Fraudfather's Dead Drop
- Posts
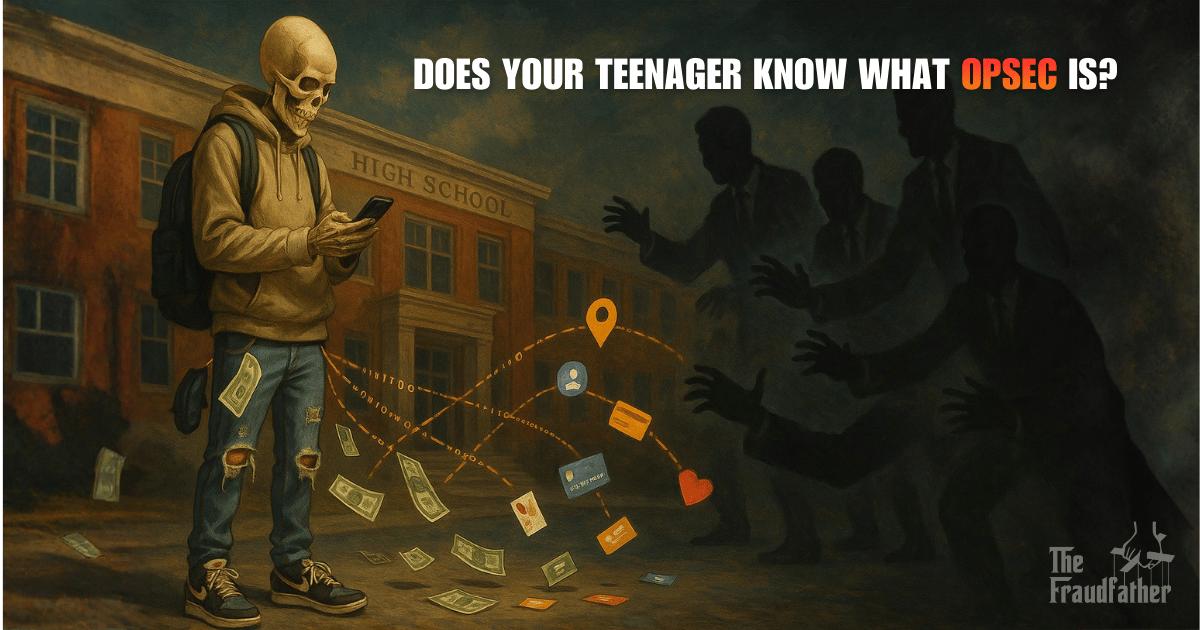
- Does Your Teenager Know What OPSEC Is? (One Didn't. Cost: $47K)
Does Your Teenager Know What OPSEC Is? (One Didn't. Cost: $47K)
Teen OPSEC failures, malware hidden in images, athletes targeted for identity theft, and crypto holders attacked at gunpoint.


Quick operational note: Fraudsters study tech obsessively. You should too. Speaking of which:.
Tech moves fast, but you're still playing catch-up?
That's exactly why 100K+ engineers working at Google, Meta, and Apple read The Code twice a week.
Here's what you get:
Curated tech news that shapes your career - Filtered from thousands of sources so you know what's coming 6 months early.
Practical resources you can use immediately - Real tutorials and tools that solve actual engineering problems.
Research papers and insights decoded - We break down complex tech so you understand what matters.
All delivered twice a week in just 2 short emails.
Teen OPSEC failures, malware hidden in images, athletes targeted for identity theft, and crypto holders attacked at gunpoint.
GM, Welcome Back to the Dead Drop.
Many years ago, I worked a case involving a 17-year-old honor student who lost $47,000 from his parents' home equity line of credit. The criminal never met him. Never called him. Never even knew his real name.
But the criminal knew everything else.
They knew which high school he attended from his Instagram location tags. They knew his gaming schedule from his Discord status. They knew his mother's maiden name from her Facebook posts celebrating their "throwback ancestry project." They knew his father traveled internationally for work from LinkedIn updates. And most importantly, they knew exactly when the family would be vulnerable, because the kid posted about his parents' anniversary trip to Cancun in real-time.
The fraud scheme? The kid received a text message claiming to be from his parents' bank's fraud department. The message said suspicious wire transfer activity had been detected on the home equity line while his father was traveling internationally, a detail that matched reality perfectly. The text included a callback number and referenced his mother's maiden name as part of the "account verification process," which made it feel legitimate. When the panicked teenager called back, the "fraud prevention specialist" knew exactly what to say: they needed to verify his identity to "stop the unauthorized transactions" before his parents' account was drained. The criminal walked him through what seemed like standard security questions, but each answer provided another piece of authentication data. Within 30 minutes, the criminal had everything needed to access the home equity line through the bank's online portal and initiated a wire transfer to a cryptocurrency exchange. By the time the parents landed in Cancun and checked their messages, the money was inflight out of their account.
The psychological pressure was calculated. The information architecture was flawless. The execution was surgical.
The kid thought he was being careful online. He had strong passwords. He used two-factor authentication. He never clicked suspicious links. But he failed at operational security, and that's what cost him.
Here's what most people miss about digital fraud in 2025: Criminals don't need to hack you anymore. You're publishing the attack surface yourself, one story, one check-in, one unthinking digital breadcrumb at a time. And teenagers, brilliant, tech-savvy, confident teenagers, are building the richest target profiles I've ever seen in two decades of investigations.
This isn't about "privacy." Privacy is an abstract concept that doesn't move people to action. This is about operational security: the specific, concrete practices that separate masters from victims. It's about understanding that every digital action creates intelligence that criminals weaponize for profit.
Several readers have asked me how to protect the teenagers in their lives. Today's opening story breaks down why digital opsec matters for fraud prevention, specifically. Because most security advice out there misses the criminal psychology entirely. It tells teenagers to "be careful online" without explaining what professional fraudsters are actually doing with their digital exhaust.
Let me show you how the game really works.
The Criminal Intelligence Cycle
When a sophisticated fraud operation targets teenagers and young adults, they're running a formal intelligence collection process. This isn't random. This is systematic profiling built on publicly available information.
Phase One: Target Identification Criminals use automated tools to scrape social media platforms for specific markers. They're looking for indicators of wealth, behavioral patterns, and most critically, poor compartmentalization. A teenager who uses the same username across Instagram, TikTok, Discord, and Reddit? That's a linked identity ripe for full-profile development.
Here's what most people don't understand: Professional fraudsters build "link analysis charts": the same tools I used in federal investigations. They map your digital presence by connecting seemingly unrelated accounts through shared usernames, email patterns, posting times, interest overlaps, and friend network intersections.
One username connects to a Reddit history discussing your parents' income. Another shows your school and graduation year. A third reveals your gaming schedule and friend group. Separately, these data points are meaningless. Connected, they become an operational blueprint for social engineering attacks.
Phase Two: Profile Enhancement Once criminals identify a promising target, they move to deep research. This is where most teenagers unknowingly provide everything required for identity theft and fraud:
Your Instagram stories show your daily routine, your location patterns, and your family's financial indicators: the car in the driveway, the vacation destinations, the birthday gifts. Your Venmo transactions? Those are public by default, revealing your friend network, spending habits, and transaction patterns. Your Discord conversations about gaming setup purchases tell criminals exactly which "account suspension" scam to run. Your TikTok videos with your school logo in the background narrow your location to a specific building.
Criminals then cross-reference this against public records: property ownership, business registrations, family connections. Remember my case with the $47,000 loss? The criminal found the parents' home equity line through public property records, then engineered a scenario where the teenager would "verify" his identity by providing the exact information needed to access it.
Phase Three: Attack Vectoring With a complete profile built, criminals design precision social engineering attacks. They know your psychology, and they exploit compartmentalization failures in ways most people never consider.
If you've kept your real identity separate from your pseudonymous Reddit account where you've posted about anxiety, relationship problems, or family conflicts? Criminals find those separations through metadata analysis, language pattern matching, and temporal correlation of posting times. Then they use that private information in targeted phishing attacks that feel impossibly personal.
A teenager receives an email that references their anonymous Reddit posts about college stress. The email appears to be from their school counselor. The link goes to a credential-harvesting site that looks identical to the school portal. Boom: compromised.
The Cascading Failure Model
Here's the operational reality that most security advice misses: Teenagers don't fail at one thing. They experience cascading compromises that start small and end catastrophic.
It begins with password reuse. You use the same password for your "throwaway" account on some random gaming forum. That forum gets breached, and they always get breached eventually. Your credentials end up on the dark web. Criminals test those credentials against your Instagram, Snapchat, email accounts.
One works. Now they're inside your ecosystem.
With access to your main email, they reset passwords for connected accounts. They search your email history for financial information, password reset links, two-factor authentication codes sent via email instead of authenticator apps. They find your school email in your contacts. They find your parents' names in family newsletters. They find your partial Social Security number from that college application document you emailed yourself.
From one compromised password on one meaningless account, criminals now have everything required for synthetic identity fraud: your real name, date of birth, partial (or full) SSN, parent information, and current address from your Amazon order confirmations.
But here's what actually destroys victims: the compartmentalization failure.
Think of your online life like rooms in a house. Each room should have a separate key. If someone breaks into one room, they can grab everything there, but they shouldn't be able to run wild through your entire house. Teenagers rarely maintain these separations. Your real Gmail account is the recovery email for your pseudonymous accounts. Your main Instagram follows your finsta. Your school email is linked to your personal Discord. You've sent DMs between your accounts "just to remember the username."
Every one of those connections creates a bridge that criminals exploit. Compromise one account, access the network. This is why I've investigated cases where a single TikTok account hack led to college application sabotage, financial fraud against parents, and even blackmail schemes, because nothing was actually separated.
Why This Matters Beyond "Privacy"
Most teenagers hear "operational security" and think it's either paranoia or doesn't apply to them. Let me reframe this entirely:
Digital opsec is fraud prevention infrastructure.
Every time you fail to compartmentalize your online identities, you're creating attack vectors for financial fraud. Every time you reuse passwords, you're giving criminals skeleton keys to your entire digital life. Every time you post in real-time from locations, you're publishing intelligence for physical security threats.
The teenager in my opening case learned this the hard way. His parents learned it when they discovered $47,000 missing. The criminal who engineered the scheme? Never caught, because the investigation revealed no actual "hacking": just systematic intelligence collection from publicly available sources and social media that the victim freely posted.
The kid did nothing obviously wrong by typical standards. He just failed at operational security. And in 2025, that's the same as leaving your bank vault open with a sign saying "take whatever you want."
The Fraudfather Bottom Line: Your digital footprint isn't about privacy; it's about preventing criminals from building the intelligence profile they need to destroy your financial life. Every teenager needs to understand operational security, not as paranoia, but as basic fraud prevention hygiene. Because the criminals hunting them aren't random hackers: they're professional intelligence collectors who monetize poor opsec at industrial scale.
The Dead Drop reaches 5,250+ security professionals, executives, and operators who refuse to be victims. This intelligence doesn't exist anywhere else: two decades of federal investigations distilled into actionable fraud prevention protocols.
Know someone being targeted by criminals who exploit trust, authority, and systematic vulnerabilities? Forward this newsletter. The people you care about are building attack surfaces they don't even recognize.
"Whoever commits a fraud is guilty not only of the particular injury to him who he deceives, but of the diminution of that confidence which constitutes not only the ease but the existence of society."

The Fraudfather's take on the week's biggest scams, schemes, and financial felonies, with the insider perspective that cuts through the noise.
ClickFix Malware: Weaponizing Innocent Images to Bypass Every Defense
Criminals are embedding advanced malware inside innocent-looking PNG images using steganography, turning every picture into a potential weapon that bypasses traditional antivirus detection. The malware payload is encoded directly into pixel color channels, especially the red channel, making images appear completely normal to human eyes while containing executable code that reconstructs itself entirely in computer memory.
Here's the criminal innovation: Attackers secretly insert malware fragments into specific pixel color values within PNG files. A victim downloads what looks like a harmless image from a website, email attachment, or social media. When malicious scripts execute, they extract the hidden data from those pixels, decrypt it, stitch the pieces together, and reconstruct dangerous malware, LummaC2 and Rhadamanthys infostealers, directly in memory without ever writing recognizable files to disk. Traditional security tools scanning for suspicious executables miss it entirely because the malware never exists as a conventional file.
The delivery mechanisms vary. One sophisticated vector uses fake Windows Update screens displayed in full-screen web browser pages that perfectly mimic legitimate system interfaces. Victims see convincing progress bars and security warnings instructing them to press specific keys, which automatically pastes malicious commands into the Windows Run box. The commands launch mshta.exe, downloading obfuscated scripts that trigger the image-extraction process. Law enforcement disrupted portions of the infrastructure through Operation Endgame in November 2025, but the core technique remains active.
The broader threat extends beyond fake updates. Any compromised website, phishing email, or malicious advertisement can distribute these weaponized images. Users download pictures thinking they're viewing innocent content while simultaneously installing sophisticated information-stealing malware designed to harvest credentials, financial data, and personal information.
Young Pro Athletes: The Perfect Identity Theft Target
Twenty percent of NBA draft picks and 15.2% of NFL draft picks from 2020-2025 experienced suspicious credit activity, compared to the 2-3% national average. That's not a coincidence; that's systematic targeting of a nearly perfect victim profile.
Here's why young athletes are fraud gold: They're 18-23 years old with thin credit histories, inconsistent digital footprints, and suddenly massive wealth. Their names, birthdays, family information, and biographical details are plastered across sports websites and social media. They move constantly between home, college, training camps, and their draft city, which means they miss mailed credit alerts. And most critically, they lack the personal protection infrastructure and financial life skills to defend against professional criminals.
The fraud mechanics are straightforward. Criminals need basic information: name, current address, birthday, family details, and a Social Security number. SSNs are traded so frequently on the dark web they're essentially commodity items. Athletes competing to go pro have zero privacy; their entire lives are public intelligence reports waiting to be weaponized.
The execution? Criminals apply for credit cards, auto loans, and consumer lending in the athlete's name. Some institutions require live video verification where applicants move their heads to prove identity, but that's trivially defeated with AI deepfakes created from publicly available photos. In one Louisiana case, two suspects were arrested attempting to take out loans while posing as Cam Ward, the 2025 first overall draft pick, and his father.
The data suggests this isn't organized crime; it's amateur criminals exploiting easy targets who broadcast every piece of personal information required for synthetic identity fraud.
Crypto Wrench Attacks: When Digital Wealth Meets Physical Violence
A San Francisco homeowner lost $11 million in cryptocurrency Saturday morning when a criminal posing as a delivery driver gained entry to his residence, pulled a gun, bound him with duct tape, and forced him to surrender wallet credentials along with his laptop and phone. The attack occurred at 6:45 a.m. in the Mission Dolores neighborhood, with the suspect exploiting the universal trust signal of delivery personnel to breach the victim's security perimeter.
This represents a fundamental shift in cryptocurrency threat modeling. Criminals have recognized that digital security means nothing when physical coercion provides direct access to credentials. The attack vector is brutally efficient: once wallet credentials are obtained under duress, crypto transfers execute within minutes, especially when routed through privacy-focused services that make tracking nearly impossible.
Security researcher Jameson Lopp's database documents over 60 "wrench attacks" globally this year, roughly double last year's total, averaging more than one per week. Recent incidents include the murder of Russian crypto promoter Roman Novak and his wife in the UAE by men posing as investors, and the kidnapping of a Chinese victim in Thailand by four suspects who extracted over $10,000 in cash and crypto.
Cybercrime consultant David Sehyeon Baek confirms the operational reality: "Identifying the suspects is usually far more achievable than recovering the stolen crypto." Coerced transfers bypass exchange security protocols that might flag suspicious digital-only thefts. The cryptocurrency moves before investigators can freeze anything.
The criminal innovation isn't technical; it's psychological. Why hack wallets when you can hack the humans who control them?
The Fraudfather combines a unique blend of experiences as a former Senior Special Agent, Supervisory Intelligence Operations Officer, and now a recovering Digital Identity & Cybersecurity Executive, He has dedicated his professional career to understanding and countering financial and digital threats.
This newsletter is for informational purposes only and promotes ethical and legal practices.


