- The Fraudfather's Dead Drop
- Posts
- Schemes, Scams, and Silicon Valley: Pardons, Power Plays, and the Cost of Complacency
Schemes, Scams, and Silicon Valley: Pardons, Power Plays, and the Cost of Complacency
The Fraudfather’s Dead Drop: Power, Pardons, and the Price of Ambition
Ambition unchecked becomes audacity, and audacity without consequence becomes power. This week, against the backdrop of controversial presidential pardons, we dissect the tactics of those who manipulate the system to their advantage. From Silicon Valley’s moral bankruptcy to the unholy alliance between Big Tech and fraudsters, power dynamics remain as ruthless as ever.
In this week's issue:
The Messiah of Moral Bankruptcy 🚘: Anthony Levandowski's rise, fall, and the pardon that rewrote the rules of Silicon Valley.
The Blame Game ⚖️: How Big Tech, banks, and regulators leave you footing the bill for scams.
Pig Butchering Exposed 🐖: The dark mechanics of romance scams turned crypto schemes.
Criminal Wisdom 💡: Lessons in dominance and deception from John Gotti and Paul Castellano.
Pandemic Fraud Fallout 💸: When government relief became a feeding frenzy for fraudsters.
Deception is an art. Understanding it is your weapon. Let’s uncover the game—and control it.
“If you see fraud and do not say fraud, you are a fraud.”
Between 2018 and 2022, the federal government hemorrhaged an estimated $233 to $521 billion annually to fraud—a number staggering enough to turn even cynics into alarmists. But what’s more unsettling is that much of this theft was no accident of mismanaged bureaucracy; it was orchestrated with precision, exploiting systemic loopholes and our collective inattention.
Consider this: over 80% of U.S. dollars in circulation today were printed since 2020, largely to prop up pandemic-era relief programs. While this liquidity saved livelihoods, it also fueled an unprecedented wave of fraud. The GAO estimates pandemic unemployment and business loan fraud alone accounts for $200 to $300 billion, a sum greater than the GDP of many nations.
The irony is bitter—money created to preserve prosperity became the golden opportunity for fraudsters to siphon it away. When oversight was weakest, predators feasted. These losses aren’t just financial; they’re existential, eroding trust in institutions and leaving victims—both taxpayers and legitimate businesses—bankrupt, while opportunists thrive. Fraud isn’t just a crime; it’s a mirror, reflecting the rot in systems too slow to adapt and too reluctant to act.
The question, as always, isn’t whether we’ll pay the price—it’s whether we’re willing to stop writing the check.

He said his community was exclusive—walls, guards, the whole package. Just forgot to mention the barbed wire.
FRAUDSTER(s) OF THE WEEK
The Wolves Among the Sheep: State Employees and the $7.2M PPP Fraud Circus
When the federal government flung open the vaults in 2020 to stem economic collapse, the Paycheck Protection Program was meant to be a life raft for drowning businesses. Instead, it became a cash buffet where opportunists queued with impunity. Nowhere is this clearer than in Illinois, where a state watchdog uncovered $7.2 million in fraud, implicating more than 275 public employees, most of whom worked for the Illinois Department of Human Services (IDHS).
Picture this: IDHS employees—whose day job involves helping the vulnerable—exploiting pandemic relief designed to save livelihoods. A barber's whispered tip here, a Facebook “opportunity” there, and suddenly public servants found themselves moonlighting as phantom business owners with $20,000 checks to prove it. Entire offices operated like mini Ponzi networks, with coworkers recruiting one another, spreading schemes like gossip over coffee breaks.
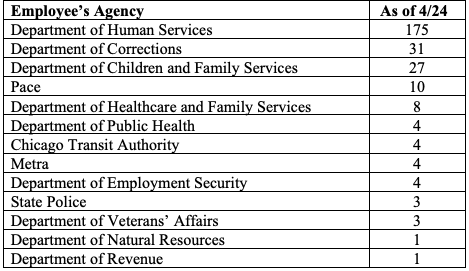
Illinois Open Fraud Cases by Agency
Take the case of Deborah Reynolds-Jones, a caseworker who outsourced her moral compass to a shady “loan consultant” for a $3,000 fee. Or Shanythia Anderson, a mental health technician, who split her fraudulent $20,000 loan with a Facebook contact, apparently unaware she was underwriting her own demise. It’s less “organized crime” and more “coordinated incompetence”—or, perhaps, desperate opportunism.
Of course, Illinois isn’t unique in this plague of ethical rot. The PPP’s design—self-certification with little oversight—was a fraudster’s utopia. When 93% of loans were forgiven and oversight lagged behind the tidal wave of cash, it was as if the program had been drafted with one hand and looted with the other. Illinois merely serves as a reminder: if the wolf is hungry enough, he will find his way into the fold.
The Fraudfather’s Take:
Fraud Breeds in Complacency:
The pandemic-era rush to disburse relief funds—paired with lax oversight—didn’t create fraudsters; it revealed them. The sheer volume of PPP fraud underscores a painful truth: systems that prioritize speed over accountability are fertile breeding grounds for exploitation.
Moral Contagion is as Dangerous as the Fraud Itself:
When wrongdoing becomes normalized—whether in a workplace, community, or crisis—ethical lines blur. Peer recruitment at IDHS highlights how misconduct spreads like a virus, turning coworkers into co-conspirators and systems into enablers.
Third-Party Actors Exploit ‘Hands-Off’ Participants:
The rise of fraudulent “loan consultants” shows how opportunists prey on ignorance and desperation. Victims-turned-actors may not see themselves as criminals—“I just signed the form”—but they’re left holding the bag when the hammer falls.
Oversight Delayed is Accountability Denied:
While watchdogs like OEIG play catch-up, billions have already disappeared. Fraud schemes, especially those rooted in federal programs, move faster than bureaucracy. Any future response must balance urgency with structural resilience to prevent repeat performances.
When Trust in Public Institutions Cracks, Everyone Loses:
Government employees exploiting federal aid isn’t just a financial scandal—it’s an erosion of trust. The damage ripples outward, casting doubt on relief programs, undermining public faith, and punishing the genuinely vulnerable who should have benefitted.
Fraud Recovery is Expensive and Reactive:
By the time fraud is identified, much of the money is unrecoverable, and taxpayers are left footing the bill. This raises an unsettling question: How do we prioritize fraud prevention in systems built for crisis?
The Line Between Victim and Perpetrator Blurs:
Many implicated employees didn’t mastermind the fraud; they were lured in by promises of easy money and plausible deniability. The trend exposes how fraudsters weaponize ignorance and trust, leaving those who “just signed” vulnerable to prosecution.
Emergencies Reveal Who We Really Are:
Crises like the pandemic serve as ethical stress tests for individuals and institutions alike. In Illinois, the temptation to exploit a broken system proved too strong for hundreds, reminding us that desperate times expose more than just financial vulnerabilities—they expose character.
The Fraudfather’s Take:
In the shadow of $7.2 million in misappropriated funds lies the far darker truth of moral contagion. Public employees entrusted to uphold the system instead exposed its weakest joints, seduced by easy money and peer complicity. Pandemic fraud didn’t just empty coffers; it eroded faith in institutions, replacing trust with cynicism. As I’ve said before, when oversight vanishes, opportunists feast—and when the buffet closes, the weakest pay the bill.
Perhaps it’s time we stop marveling at how brazen fraudsters are and instead ask how they became so comfortable under the spotlight. The pandemic didn’t just expose vulnerabilities; it illuminated our willingness to exploit them.
PIG BUTCHERING
Tactic 1: The Slaughterhouse of Deceit: How Pig Butchering Scams Are Gutting Global Wealth
How It Works:
Emotional Harvesting:
Scammers initiate contact via dating apps, social media, or messaging platforms. They build emotional intimacy, creating the illusion of trust and shared goals, often feigning romantic interest. Victims are "fattened" with constant attention, affection, and fabricated life stories.
The Baited Opportunity:
Once trust is secured, scammers introduce a "can’t-miss" investment opportunity. Cryptocurrency trading platforms are the current weapon of choice. These platforms are often custom-built by the scammers, giving victims a false sense of legitimacy through polished interfaces and fake testimonials.
Simulated Success:
Victims see fabricated gains in their "accounts," encouraging them to invest more. Scammers exploit the sunk-cost fallacy, knowing the more someone invests, the harder it becomes for them to walk away.
The Butcher’s Knife:
When victims attempt to withdraw funds, scammers demand fees, taxes, or "security upgrades," bleeding them further. At this point, victims often realize the betrayal, but the psychological and financial damage has already been inflicted.
Beyond the Initial Cut:
Victims who attempt to sever ties are often extorted with threats of exposing personal data or compromising photos (sextortion). Others are unknowingly roped into becoming mule accounts, furthering the fraud cycle by laundering money for the scammers.
Real-World Evolution:
Global Crime Hubs:
Recent reports from Nigeria revealed an entire "scam hub" of 800 fraudsters targeting victims worldwide, illustrating the industrial scale of pig butchering operations.
Cultural Shaming:
In some regions, victims hesitate to report the crimes, fearing societal judgment. Being labeled a "pig" is a double humiliation, as fraudsters exploit cultural values of pride and privacy to silence their victims.
Advanced Tech Integration:
Scammers increasingly leverage AI tools to create hyper-realistic personas, using deepfake voices and videos to build authenticity. These advancements amplify the scale and effectiveness of their deception.
Defense Strategies:
Validate Connections:
Research photos and profiles through reverse image searches and online reputation tools. Scammers frequently reuse stolen identities.
Guard Against Financial Manipulation:
Avoid investment schemes promoted by new online connections. Consult trusted financial advisors or verified platforms before committing any funds.
Recognize Red Flags:
Unsolicited investment advice.
Sudden romantic or personal interest from strangers online.
Claims requiring urgent financial decisions.
Secure Personal Information:
Protect your social media profiles and limit the personal details you share publicly. Scammers craft narratives tailored to your vulnerabilities.
Report Early and Often:
Contact law enforcement and agencies like IC3 or local cybercrime divisions if you suspect foul play. Early reporting prevents further harm and flags platforms used by scammers.
The Fraudfather's Take:
Pig butchering scams represent a masterclass in human manipulation. These fraudsters aren’t just stealing money—they’re hijacking identities, exploiting emotions, and weaponizing technology to strip their victims of both dignity and savings. The cruel irony is that victims often blame themselves, while the true culprits move on to the next "farm."
Here’s the unvarnished truth: no one is immune. In a world where AI can craft fake lovers and crypto promises overnight wealth, the only way to stay ahead is to cultivate skepticism as a survival skill. Protect your wealth by mastering the tactics of those who seek to exploit it.
Remember, the fattest pigs in this slaughterhouse are the ones who trust too easily. Don’t be on the menu.
Book a Call with the Fraudfather! to fortify your defenses today!
SCAMS
Tactic #2: The Blame Game – Who Pays When the Fraudsters Win?
How It Works:
Shift the Liability: Fraudsters exploit the gaps between Big Tech, banks, and regulators to scam consumers. When fraud occurs, disputes arise over who bears the cost—leaving victims caught in the crossfire. Financial institutions blame platforms for hosting scammers, while tech companies argue they’re just intermediaries.
Exploiting Consumer Trust: Fraudsters thrive on the inherent trust people place in recognizable platforms like social media sites, online marketplaces, and payment apps. By mimicking legitimate entities or creating fake profiles, they lure victims into a false sense of security.
Regulatory Loopholes: Current U.S. policies don’t mandate reimbursement for scam-induced fraud losses, leaving many victims with no recourse. In 2023, U.S. consumers lost over $10 billion to scams, yet the legal framework is ill-equipped to handle the scale or complexity of modern fraud.
Pushing the Burden: Banks in the U.S. are increasingly adopting stringent fraud-prevention measures, but Big Tech platforms continue to profit from their ecosystems without bearing the cost of scam fallout. Meanwhile, consumers remain largely unprotected.
Real World Evolution:
This tactic has evolved in the U.S. as fraudsters capitalize on the decentralized accountability of the digital age. Unlike the UK, where banks may reimburse victims in certain scams, U.S. financial institutions often require victims to demonstrate negligence by the platform—a nearly impossible task given the speed and sophistication of scams. With banks lobbying for greater Big Tech accountability, the debate over liability intensifies.
Defense Strategies:
Verify Before You Trust:
Independently verify messages, offers, or links received through social media or email by contacting the organization directly via official channels.
Avoid engaging with unsolicited messages or friend requests, especially those making financial claims.
Leverage Multi-Layered Protections:
Use two-factor authentication (2FA) for all sensitive accounts to prevent unauthorized access.
Regularly review account activity and freeze your credit if suspicious activity is detected.
Push for Platform Accountability:
Advocate for stronger regulatory measures requiring tech platforms to prevent scams and share responsibility with financial institutions.
Educate and Empower:
Report fraud attempts to the FTC and FBI’s Internet Crime Complaint Center (IC3).
Spread awareness among friends and family, emphasizing skepticism and proactive cybersecurity practices.
The Fraudfather’s Take:
The Golden Age of Scams has illuminated a critical power dynamic: whoever controls the platform controls the narrative. As Robert Greene’s 48 Laws of Power suggests, “Control the options: Get others to play with the cards you deal.” Big Tech and financial institutions are masters of this game, shifting liability away from themselves to the consumer. For fraudsters, these gaps are an open door.
To adapt, channel Robert Cialdini’s principle of reciprocity. Pressure these entities to give back—demand accountability from the platforms and banks profiting from the systems that scammers exploit. True power lies in collective action and exposing the cracks in their well-oiled defenses. Remember: in this game, knowledge isn’t just power—it’s survival.
Criminal Insights
“Don't carry a gun. It's nice to have them close by, but don't carry them. You might get arrested.”
John Gotti, the so-called "Teflon Don," was a larger-than-life figure who epitomized the brash, unapologetic power of the Gambino crime family during the 1980s. Known for his sharp suits, charisma, and penchant for public displays of wealth, Gotti ascended to the role of boss through a ruthless coup, orchestrating the murder of his predecessor, Paul Castellano. Despite facing repeated indictments, his knack for jury tampering and witness intimidation earned him his infamous nickname as charges seemed to slide off him. However, Gotti’s flamboyant lifestyle and thirst for media attention made him a target for law enforcement, leading to his downfall when his underboss, Sammy "The Bull" Gravano, turned state's witness. Gotti’s conviction in 1992 marked the end of an era for the Mafia, but his legacy as a cultural icon of organized crime endures—a blend of menace, magnetism, and hubris.
“There are certain promises you make that are more sacred than anything that happens in a court of law, I don't care how many Bibles you put your hand on.”
Paul Castellano, often referred to as "Big Paul," was a controversial figure who led the Gambino crime family with a veneer of corporate sophistication that masked his ruthless ambition. A towering presence both physically and in the mob hierarchy, Castellano rose to power in 1976, succeeding his brother-in-law Carlo Gambino. Known for his preference for white-collar rackets over traditional street-level crimes, Castellano sought to modernize the Mafia, emphasizing profit over bloodshed. However, his aloof demeanor, extravagant Staten Island mansion dubbed the "White House," and rumored dalliance with his maid alienated many within his ranks. His detachment from the gritty realities of mob life ultimately led to resentment, culminating in his infamous 1985 assassination outside Sparks Steak House—a bold, brazen hit orchestrated by John Gotti. Castellano's downfall marked a violent turning point for the Gambino family and the broader landscape of organized crime.

Behind the glowing screens and encrypted files, a world of corporate espionage unfolds—where ambition meets betrayal in the race for technological dominance.
Anthony Levandowski: The Self-Driving Messiah of Silicon Valley’s Moral Bankruptcy
The tech world has its icons, its innovators, and then its Anthony Levandowskis—a man whose name became synonymous with ambition so audacious it shattered the boundaries of corporate ethics. With the current administration unveiling a fresh wave of controversial pardons, it feels almost poetic to revisit Levandowski’s saga. From Google’s Waymo to the courtroom dock, and finally to the velvet absolution of a presidential pardon, his story is not merely one of stolen trade secrets or self-driving cars. It’s a Silicon Valley thriller, complete with betrayal, espionage, and a deus ex machina ending. Levandowski’s arc is a study in power, persuasion, and the human impulse to risk everything for control of the future—even as the weight of 14,000 stolen files threatened to end it all.
The Rise: Building the Roads to Tomorrow
Born in Brussels and educated at UC Berkeley, Levandowski quickly ascended the tech hierarchy as a wunderkind of robotics and machine learning. His tenure at Google’s self-driving division, Waymo, positioned him as a trailblazer in autonomous vehicles. But like all men who dare to create their own empires, Levandowski grew restless. He believed his genius deserved more than a corporate salary and a polished LinkedIn profile—it deserved control.
In 2016, Levandowski left Waymo under a storm cloud of suspicion, taking with him trade secrets that would later underpin his startup, Otto. Uber, always hungry for disruption, acquired Otto for a staggering $680 million, crowning Levandowski as Silicon Valley’s most controversial golden child.

Anthony Levandowski
The Fall: From Tech Titan to Courtroom Spectacle
Google’s discovery of Anthony Levandowski’s alleged theft was the stuff of corporate espionage lore. The company noticed suspicious overlaps between the designs and concepts at its self-driving division, Waymo, and those appearing in Uber’s nascent autonomous vehicle efforts. The tipping point came when a Waymo employee was inadvertently copied on an email from a supplier that included an Uber lidar circuit design. This design bore an uncanny resemblance to Waymo’s proprietary technology. Digging deeper, Google’s internal investigation revealed that Levandowski had downloaded 14,000 confidential files, including detailed schematics, just before leaving to form Otto, his self-driving truck startup later acquired by Uber. What began as a hunch spiraled into a legal battle exposing a web of betrayal and trade secret theft at the cutting edge of autonomous vehicle innovation.
Levandowski’s hubris caught up with him when Waymo sued Uber, exposing a web of deceit spun from stolen trade secrets. The lawsuit peeled back the curtain on a tech world where intellectual property was not just stolen—it was weaponized. Levandowski became the poster child for Silicon Valley’s moral elasticity, a living embodiment of Robert Greene’s Law 15: Crush Your Enemy Totally. Waymo crushed him. By 2020, he was convicted of theft and sentenced to 18 months in prison.
But Levandowski’s story didn’t end with a prison cell. Instead, it took a turn straight out of Robert Cialdini’s Influence: the principle of Authority. Levandowski’s deep ties to tech elites like Peter Thiel paid dividends when, in the final hours of the Trump administration, he was granted a pardon. It was a move that left ethics professors clutching their pearls and Levandowski walking free to reimagine himself yet again.

Peter Thiel: Visionary entrepreneur and master strategist, reshaping the frontiers of technology and finance with his audacious intellect.
The Art of Tech Espionage: How It Works
Levandowski’s exploits offer a blueprint for navigating the treacherous waters of intellectual property theft in the digital age:
Corporate Espionage: Leverage insider access to secure proprietary data. The goal isn’t just theft but gaining an edge so sharp it cuts through competitors' profits.
Strategic Partnerships: Align with entities that benefit from your secrets. Uber’s acquisition of Otto was less about trucks and more about accelerating their war against Waymo.
Plausible Deniability: Maintain a veneer of innocence while orchestrating complex schemes. Levandowski claimed ignorance even as 14,000 files sat like a loaded gun on his servers.
Fraudfather’s Note: Levandowski and the Laws of Power
Levandowski’s life is a clinic in power dynamics, a dazzling dance of persuasion and control that aligns with Greene’s and Cialdini’s seminal works:
Law 6: Court Attention at All Costs: Levandowski’s every move ensured his name dominated headlines. Controversy wasn’t a setback; it was a strategy.
Law 31: Control the Options: By aligning his actions with Uber’s ambitions, Levandowski positioned himself as indispensable to their fight against Waymo. Even as the legal walls closed in, his relevance kept him in play.
Law 28: Enter Action with Boldness: Levandowski didn’t tiptoe around trade secrets—he bulldozed through them, betting that Silicon Valley’s appetite for disruption would protect him.
Principle of Scarcity (Cialdini): Levandowski cultivated the perception that his knowledge was rare and irreplaceable, creating a demand that even his legal troubles couldn’t quash.
The Legacy of the Pardon
Levandowski’s pardon is more than a footnote in his story—it’s a symbol of how power protects its own. As today’s administration grapples with high-profile pardons, his case serves as a reminder that the scales of justice often tilt toward those who understand how to manipulate them.
For Levandowski, freedom wasn’t just a legal outcome—it was the final product of a strategy decades in the making. His tale stands as a beacon to those willing to flirt with chaos in the pursuit of greatness, proving that in the high-stakes world of innovation, the line between hero and villain is as blurred as the future he helped engineer.
About The Fraudfather
The Fraudfather combines a unique blend of experiences as a former Senior Special Agent, Supervisory Intelligence Operations Officer, and now a recovering Digital Identity & Cybersecurity Executive, He has dedicated his professional career to understanding and countering financial and digital threats.
Fast Facts Regarding the Fraudfather:
Global Adventures: He’s been kidnapped in two different countries—but not kept for more than a day.
Uncommon Encounter: Former President Bill Clinton made him a protein shake.
Unusual Transactions: He inadvertently bought and sold a surface-to-air missile system.
Perpetual Patience: He spent 12 hours in an elevator.
Unique Conversations: He spoke one-on-one with Pope Francis for five minutes using reasonable Spanish.
Uncommon Hobbies: He discussed beekeeping with James Hetfield from Metallica.
Passion for Teaching: He taught teenagers archery in the town center of Kyiv, Ukraine.
Unlikely Math: Until the age of 26, he had taken off in a plane more times than he had landed.
This newsletter is for informational purposes only and promotes ethical and legal practices.


