- The Fraudfather's Dead Drop
- Posts
- They're Stealing Your Money AND Hiding Your Rights
They're Stealing Your Money AND Hiding Your Rights
Inside the $300M PPP fraud that fooled thousands + the systematic campaign to make your privacy rights invisible


Inside the $300M PPP fraud that fooled thousands + the systematic campaign to make your privacy rights invisible
GM, Welcome Back to the Dead Drop.
In the world of intelligence operations, the most effective surveillance operations are the ones you never realize are happening. The best intelligence collectors don't break down your door, they convince you the door was never there in the first place.
That's exactly what's unfolding in the data broker industry right now. While Americans have been focused on obvious privacy threats like social media tracking and phone surveillance, a more insidious campaign has been quietly executing: systematically vanishing the legal mechanisms designed to protect your privacy.
This week, I'm pulling back the curtain on what I call Operation Ghost Door, a coordinated industry-wide effort to make your privacy rights functionally invisible. New congressional pressure from Senator Maggie Hassan has forced 35 data broker companies to explain why they've been using technical code to hide their legally required opt-out pages from search engines. But this is bigger than just hidden web pages. This is psychological warfare conducted at corporate scale.
Here's the intelligence briefing on how they're doing it, why domestic violence survivors are being specifically targeted, and what this teaches us about recognizing when legitimate compliance becomes criminal obstruction.
Intelligence Assessment: The Ghost Door Architecture
OPERATIONAL CLASSIFICATION: Shadow Compliance
From an operational perspective, what these data brokers have deployed is brilliant in its simplicity and devastating in its effectiveness. They've created what intelligence professionals call "functional denial," technically meeting legal requirements while operationally negating them.
Primary Attack Vectors:
The Search Invisibility Protocol: At least 35 companies deployed robots.txt files and no-index meta tags specifically to prevent search engines from finding their opt-out pages. This isn't accidental, it's systematic information warfare. They know consumers will search "CompanyName opt out" when they want to delete their data. By blocking that discovery path, they've weaponized our own reasonable expectations against us.
Think like an intelligence officer analyzing this threat pattern: They're exploiting the gap between legal compliance and operational accessibility. The law requires them to provide opt-out mechanisms. It doesn't specifically require those mechanisms to be discoverable.
The Maze Protocol: Companies like Telesign buried their opt-out forms 7,000 words deep into privacy policies filled with legalese, with no direct links from homepages. This creates what we call "exhaustion attrition," making compliance so cognitively expensive that targets abandon the mission.
The Disappearing Evidence Protocol: Here's where it gets truly operational: Five companies listed privacy pages in California's official registry that simply don't exist anymore. BrightCheck's page was archived in February, existed in March, but was gone by July when investigators checked. This is active intelligence destruction; removing evidence of compliance infrastructure once regulatory attention moves elsewhere.
The FTC's lawsuit against Kochava revealed that data brokers' geolocation data can be used to track consumers at domestic violence shelters, potentially revealing the location of people escaping abuse.
Target Analysis: Why Domestic Violence Survivors Are Primary Victims
The most disturbing intelligence in this investigation isn't technical, it's targeting. Privacy advocates and organizations supporting survivors of stalking and gendered violence have been voicing concerns for years about people search data brokers and their linkage and sale of personal information. This isn't academic concern. This is life-and-death operational reality.
High-Value Target Profile:
Domestic violence survivors are specifically vulnerable because abusers often know their intimate personal details and can exploit the general lack of protection for personal information in our society. When opt-out mechanisms are systematically obstructed, these survivors become trapped in a surveillance net they can't escape.
Threat Vector Analysis:
The FTC's lawsuit against Kochava revealed that data brokers' geolocation data can be used to track consumers at domestic violence shelters, potentially revealing the location of people escaping abuse. The data can identify mobile devices that spent nights at temporary shelters for at-risk pregnant women or new mothers.
For domestic violence survivors, a quick online search can reveal social media accounts, news stories, photos, and data broker sites selling current and former addresses, financial records, and background checks. When opt-out pages are deliberately hidden, survivors can't remove this life-threatening intelligence from circulation.
The Operational Impact: Fear of exposure by data brokers may cause survivors not to seek legal services, find new jobs, or purchase homes to avoid generating records that data brokers can obtain and sell to abusers. This creates a feedback loop: the harder it is to opt out, the more isolated and vulnerable survivors become.
Psychological Operations: The Compliance Theater Campaign
From a behavioral analysis perspective, what these companies have deployed is sophisticated psychological manipulation designed to exploit decision fatigue and learned helplessness.
The Plausible Deniability Defense: When confronted by investigators, most companies claimed the search blocking was "an oversight" and not intentional. But the speed of their corrections reveals this was policy, not accident. Nine of ten companies removed the blocking code immediately after being contacted.
This is classic operational security: maintain deniability while systematically executing the mission. The moment operational security is compromised, rapidly implement cosmetic fixes to demonstrate "good faith compliance."
The Identity Verification Trap: Here's where the psychological manipulation becomes truly predatory. Companies are requiring excessive identity verification for opt-out requests, including photographed identity documents, while simultaneously making those opt-out pages impossible to find.
The California Privacy Protection Agency fined Todd Snyder $345,178 partly for requiring consumers to provide photos holding their identity documents for simple opt-out requests. The message is clear: to protect your privacy, you must surrender even more sensitive information in a process that's deliberately designed to be abandonable.
The Exhaustion Strategy: This isn't customer service failure, it's weaponized friction. Hassan noted companies force users to "scroll through multiple screens, dismiss needless pop-ups and hunt for links in shrunken text". Each obstacle is a calculated decision point where consumers might give up and walk away.
Congressional Response: The Intelligence Counter-Operation
Senator Hassan's pressure campaign against five major firms: IQVIA Digital, Comscore, Telesign Corporation, 6sense Insights, and Findem. This represents the first coordinated congressional counter-intelligence operation against this systematic obstruction.
Hassan's Tactical Approach: Her letter demands companies:
Justify why code on their sites appears designed to frustrate deletion requests
Acknowledge if they used code to block search indexing and against how many users
Pledge to remove blocking code by September 3rd
Provide Congress with audit results and improvement steps
This is classic intelligence gathering: forcing disclosure of operational methods, scale of impact, and remediation timelines. It transforms covert operations into documented admissions.
The Regulatory Escalation: The Consumer Financial Protection Bureau has proposed rules to limit data brokers selling sensitive personal information to "scammers, stalkers, and spies", while the California Privacy Protection Agency has reached settlements with multiple data brokers, with fines starting at $200 per day for non-compliance.
The operational pressure is increasing. Regulators are conducting investigative sweeps and promising that "for data brokers skirting the law, the fine increases with each passing day."
Field Manual: Ghost Door Detection and Breach Protocols
Based on this intelligence assessment, here are the operational protocols for detecting and defeating these systematic obstruction campaigns:
Technical Intelligence Gathering:
Conduct parallel searches: company name + "opt out", "delete data", "privacy rights"
Cross-reference results with California's official data broker registry listings
Check company.com/robots.txt for blocked privacy-related URLs
Use site-specific searches:
site:company.com "do not sell"
Behavioral Pattern Analysis:
Time how long it takes to locate opt-out mechanisms versus sign-up processes
Count the number of clicks required for privacy-protective choices versus data-sharing choices
Document identity verification requirements that exceed legal necessity
Historical Intelligence:
Use Wayback Machine to check if opt-out pages existed previously but were removed
Search privacy forums for screenshots of company opt-out processes
Check if pages listed in regulatory databases return errors or don't exist
🚨 OBSTRUCTION INDICATORS:
Systematic Concealment Patterns:
Opt-out pages invisible to search engines while other company content is indexed
Generic page titles that don't match user search intent ("Information Governance" vs "Opt Out")
URLs using obscure paths (/ig/ig-7 instead of /opt-out or /delete)
Process Weaponization:
Identity verification requiring sensitive documents for simple deletion requests
Multi-step processes for saying "no" versus single-click processes for saying "yes"
Contact forms that appear to submit but never generate confirmations
Psychological Manipulation:
Excessive legal jargon designed to exhaust rather than inform
Pop-ups and dismissible elements that interrupt opt-out flows
Warning language that overstates consequences of privacy protection
BREACH AND ESCALATION TACTICS:
Direct Action:
Construct standard opt-out URLs manually (/opt-out, /privacy-choices, /delete-data)
Access blocked pages through cached versions or archive services
Use company contact information to request opt-outs via email or phone
Documentation Warfare:
Screenshot every step of attempted opt-out processes
Record timestamps showing delays or failures
Save confirmation emails (or lack thereof) as evidence
Regulatory Engagement:
File complaints with California Privacy Protection Agency for dark pattern violations
Report companies hiding opt-out pages to appropriate state attorneys general
Submit detailed documentation to congressional representatives
The Fraudfather Bottom Line
Sean Vitka from Demand Progress compared the surveillance ecosystem underlying commercial data markets to "the knotted tails of a rat king, an inseparable tangle of entities sustained by unchecked data flows". His assessment: "The industry cannot be trusted to mitigate its own harms."
The Strategic Reality: California's Delete Request and Opt-out Platform (DROP) will launch in 2026, allowing consumers to send deletion requests to all registered data brokers simultaneously. The industry knows their obstruction tactics have an expiration date, which explains the aggressive implementation now.
The Operational Truth: This isn't incompetence, it's systematic information warfare. The speed with which companies "fixed" their blocking code after media attention proves this was deliberate policy. They're maximizing data extraction while they still can.
The National Security Dimension: Countries like China and Russia can purchase detailed personal information about military members and government employees for "pennies per person," enabling sophisticated intelligence operations. When opt-out mechanisms are deliberately sabotaged, Americans can't protect themselves from foreign intelligence collection.
The Human Cost: For domestic violence survivors, data broker obstruction isn't just privacy invasion, it's potential physical endangerment. Every hidden opt-out page potentially keeps a survivor visible to their abuser.
Your defense against Ghost Door operations isn't paranoia, it's understanding that systematic obstruction is an operational choice, not a technical accident. When companies make exercising legal rights feel impossible, they've crossed from compliance into psychological warfare.
A Private Circle for High-Net-Worth Peers
Long Angle is a private, vetted community for high-net-worth entrepreneurs, executives, and professionals across multiple industries. No membership fees.
Connect with primarily self-made, 30-55-year-olds ($5M-$100M net worth) in confidential discussions, peer advisory groups, and live meetups.
Access curated alternative investments like private equity and private credit. With $100M+ invested annually, leverage collective expertise and scale to capture unique opportunities.


The Fraudfather's take on the week's biggest scams, schemes, and financial felonies, with the insider perspective that cuts through the noise.
The Trust Thieves: How a News Anchor and Her Husband Stole $300 Million in Plain Sight
While you were worried about traditional bank robberies, a different kind of heist was unfolding. No masks, no guns, just a laptop, fabricated documents, and the perfect cover story about "helping small businesses survive the pandemic."
Meet Stephanie Hockridge and Nathan Reis, the husband-and-wife team behind Blueacorn, who turned COVID relief into their personal ATM. Their fintech company processed $12 billion in Paycheck Protection Program loans, but prosecutors say they systematically defrauded the government while pocketing nearly $300 million.
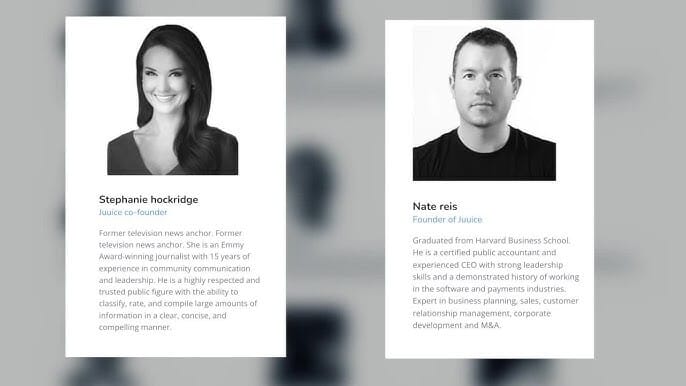
Meet Stephanie Hockridge and Nathan Reis, the husband-and-wife team behind Blueacorn, who turned COVID relief into their personal ATM.
This week, we're diving deep into The Blueacorn Blueprint, a case study in how sophisticated fraudsters exploit national emergencies, manipulate legitimate business structures, and weaponize our desire to help the vulnerable.
Here's what they did that you need to understand. Here's how they almost got away with it. And here's what their downfall teaches us about recognizing predators who hide behind humanitarian facades.
The Criminal Playbook: Operation Bootstrap
Phase 1: The Perfect Storm Setup
In April 2020, as COVID-19 devastated American businesses, Reis and Hockridge founded Blueacorn with the stated mission to "democratize access to loan relief" for small businesses and independent contractors. The timing wasn't coincidental, it was calculated.
Think like a criminal for a moment. You need three elements for a successful fraud:
Massive money flow ✓ (PPP authorized $600+ billion)
Overwhelmed oversight ✓ (government prioritized speed over scrutiny)
Legitimate cover story ✓ ("We're helping struggling businesses survive")
Congress had just raised lender fees for smaller loans to incentivize banks to help businesses that were being overlooked. Blueacorn seized this opportunity, positioning themselves as the champion of the forgotten entrepreneur.
Phase 2: The Infrastructure of Deception
Here's where the Blueacorn operation gets sophisticated. They established Lender Service Provider Agreements (LSPAs) with two legitimate lenders, collecting and reviewing PPP applications on behalf of these partners in exchange for a percentage of SBA-paid fees.
This wasn't some back-alley loan shark operation, this was fraud dressed up in legitimate business attire, complete with:
Professional website and marketing materials
Real partnerships with established financial institutions
Proper regulatory filings and business registrations
A former news anchor as cofounder (instant credibility boost)
Phase 3: The VIPPP System - Fraud at Scale
Blueacorn created their "VIPPP" program for high-dollar loan applicants, providing personalized service that involved coaching borrowers on how to submit false information. The psychology here is brilliant and terrifying:
Premium positioning: Making fraud feel exclusive and professional
Personal touch: Building trust through individual attention
Plausible deniability: Framing document alteration as "application optimization"
Internal communications revealed their true priorities: "monster loans [that] will get everyone paid," while dismissing smaller, legitimate applications.
Operational Reality: The Document Factory
Let me walk you through exactly how they executed this at the tactical level, because understanding their methods protects you from similar schemes:
The Fabrication Assembly Line:
FBI Agent Collin Friedmann's testimony revealed the smoking gun evidence on Hockridge's computer: two versions of the same borrower's 1099 form, the original showing $57,000 in earnings, the fabricated version showing $157,000.
This wasn't sloppy fraud. This was systematic document manufacturing:
Tax document alteration: Using professional software to modify income figures
Bank statement doctoring: Inflating account balances and transaction histories
Payroll record fabrication: Creating entirely fictional employee rosters and wage records
The Family Network:
The investigation uncovered text messages where Hockridge coached her own father on applying for PPP loans, telling him to "come up with a side job you did for extra cash" to qualify for $60,000 in relief money.
This reveals the fraudster mindset: when you normalize criminality within your own family circle, you've crossed a psychological point of no return.
The Quality Control Problem:
In one particularly damaging message, Hockridge blamed her husband's "poor Photoshop skills" after a lender flagged an obviously altered tax document. They weren't just committing fraud, they were treating document forgery like a business process optimization problem.
The Psychology of Trust Exploitation
The Authority Transfer Method:
Stephanie Hockridge wasn't just any fraudster. She was a former ABC15 news anchor who worked at the station from 2011 to 2018. For nearly a decade, she was literally the voice people trusted to deliver the news.
Think about the psychological impact:
Credibility by association: News anchors are trained to appear trustworthy and authoritative
Community connection: Local news personalities feel like neighbors, not strangers
Professional presentation: Years of on-camera experience in maintaining composure under pressure
The Helping Hand Deception:
During the height of the pandemic crisis, the defendants positioned themselves as advocates for struggling small businesses desperately needing financial lifelines. This is textbook predator behavior, targeting victims when they're most vulnerable and desperate.
The criminal calculus here is simple:
Desperate people ask fewer questions
Grateful people are less likely to report suspicious activity
People in crisis will overlook red flags they'd normally catch
The Scale of Betrayal:
Congressional investigators found that Blueacorn and similar fintech companies facilitated nearly one in every three PPP loans funded in 2021, but failed to implement systems capable of consistently detecting and preventing fraudulent applications.
This wasn't just individual fraud, this was systematic exploitation of national emergency relief programs.
Field Manual: Red Flags in Crisis "Help"
Based on twenty years of investigating these schemes, here are the warning signs that separate legitimate crisis assistance from predatory exploitation:
🚨 IMMEDIATE RED FLAGS:
Pressure to Act Fast:
"Limited time" offers during national emergencies
Discouraging you from seeking second opinions
Creating false urgency around paperwork deadlines
Documentation "Assistance" That Goes Too Far:
Anyone offering to "optimize" your financial documents
Suggestions to overstate income, employee counts, or expenses
Requests to backdate documents or create retroactive records
Fee Structures That Don't Add Up:
Percentage-based fees that increase with loan amounts
Upfront payments for "guaranteed approval"
Hidden kickbacks or referral arrangements
DEEPER INVESTIGATION PROTOCOLS:
Verify Independently:
Cross-check company registration with state databases
Confirm professional licenses and certifications
Research principals' backgrounds through multiple sources
Follow the Money Trail:
Understand exactly how fees are calculated and paid
Verify all financial institution partnerships directly
Question any complex payment arrangements or third-party transfers
Document Everything:
Maintain original copies of ALL financial documents
Record all communications and advice given
Create detailed timeline of application process
The Fraudfather Bottom Line
Since the COVID-19 Fraud Enforcement Task Force was established in 2021, DOJ has charged over 3,500 defendants and recovered more than $1.4 billion in fraudulently obtained relief funds. In fiscal year 2024 alone, over 250 False Claims Act settlements and judgments resulted in more than $250 million in pandemic fraud recoveries.
But here's what the statistics don't capture: the psychological damage done when people lose faith in legitimate emergency assistance programs.
Every Stephanie Hockridge and Nathan Reis who exploits a crisis makes it harder for real victims to get real help. They don't just steal money, they steal trust in institutions designed to protect us when we're most vulnerable.
CRITICAL INTELLIGENCE: Congress extended the statute of limitations for PPP fraud from 5 to 10 years (the Fraudfather testified in Congress in support of this), meaning criminal charges and civil enforcement can continue until 2031. The investigation phase is far from over.
The Strategic Takeaway: When national emergencies create new funding programs, they also create new hunting grounds for sophisticated predators. The criminals who succeed aren't the desperate amateurs, they're the ones who build legitimate-looking businesses around systematic fraud.
Your defense isn't paranoia about all assistance programs. Your defense is understanding how trust-based fraud operates, maintaining healthy skepticism during crisis periods, and knowing the specific tactics predators use to separate you from accurate judgment.
Quick Reference: Crisis Fraud Protection Protocol
✓ VERIFICATION CHECKPOINTS:
Independent research on company principals and track record
Direct confirmation of all partnership claims and credentials
Multiple source validation of program requirements and limitations
Professional review of any document modification suggestions
✗ IMMEDIATE DISQUALIFIERS:
Pressure to falsify or "optimize" financial information
Fees that scale with assistance amounts rather than services provided
Discouragement from consulting attorneys, accountants, or other advisors
Requests for upfront payments before services are confirmed legitimate
🎯 MONITORING ACTIONS:
Maintain detailed records of all interactions and advice received
Regular verification that submitted information remains accurate
Ongoing tracking of fund usage and program compliance requirements
Immediate reporting of any suspicious requests or pressure tactics
The most dangerous fraud schemes don't look like fraud, they look like help. Your survival depends on knowing the difference.
The Fraudfather investigates. You stay protected.
The Fraudfather combines a unique blend of experiences as a former Senior Special Agent, Supervisory Intelligence Operations Officer, and now a recovering Digital Identity & Cybersecurity Executive, He has dedicated his professional career to understanding and countering financial and digital threats.
This newsletter is for informational purposes only and promotes ethical and legal practices.


