- The Fraudfather's Dead Drop
- Posts
- 🚨 The $1.5 Billion Heist No One Can Stop—And the AI Scam That’s Coming for You Next 🚨
🚨 The $1.5 Billion Heist No One Can Stop—And the AI Scam That’s Coming for You Next 🚨
They don’t break in—they log in. The greatest frauds aren’t smash-and-grab jobs; they’re precision heists, psychological warfare, and digital deception at scale.itle
🚨 The $1.5 Billion Heist No One Can Stop—And the AI Scam That’s Coming for You Next 🚨
Fraud isn’t just evolving—it’s winning. From deepfake-driven romance scams to state-sponsored crypto heists, the modern con is bigger, smarter, and more profitable than ever. This week, we break down the biggest financial crimes shaking the world—and the dark psychology behind them.
Inside This Week’s Dead Drop:
🔹 North Korea’s $1.5 Billion Crypto Heist – The Lazarus Group just pulled off the biggest crypto robbery in history. But this isn’t just a crime—it’s a funding mechanism for nuclear weapons. How did they do it? And more importantly, why is the crypto world powerless to stop them?
🔹 Deepfake Love: The AI-Powered Romance Scam Epidemic – If you think you can trust a video call, think again. AI-generated lovers are draining bank accounts worldwide, and the scams are getting terrifyingly real. Here’s how they work—and how to fight back.
🔹 Hacking Charisma: The CIA’s Playbook for Influence – Influence isn’t luck; it’s science. The best manipulators—spies, con artists, and power players—use proven psychological exploits to get what they want. Learn their tactics before they use them on you.
🔹 Cognitive Warfare: The Mind Hacks That Shape Your Decisions – Why do people say yes when they should say no? Why do we obey authority, even when it’s wrong? And how can you spot—and resist—psychological manipulation in real time?
Fraud is deception, misdirection, and control. The best analysts don’t see what they expect—they see what’s real. Do you?
Let’s get to work.
📞 Need a privacy overhaul? Book a Call with the Fraudfather! to fortify your defenses today!
"There are no innocent men—only those whose crimes are too small to matter. The difference between a king and a conman, a banker and a thief, a tyrant and a savior is who gets to rewrite the rules after the heist. Power doesn’t punish fraud; it refines it."
Fraud’s Hall of Infamy: North Korea's $1.5 Billion Bybit Heist—A Regime's Digital Pillage
In the shadowy corridors of global finance, where lawlessness masquerades as innovation, North Korea has once again asserted its dominance. The recent $1.5 billion heist from cryptocurrency exchange Bybit isn't merely a breach of digital security; it's a brazen act of economic warfare, funding a regime that thrives on the world's inattention and the crypto industry's hubris.
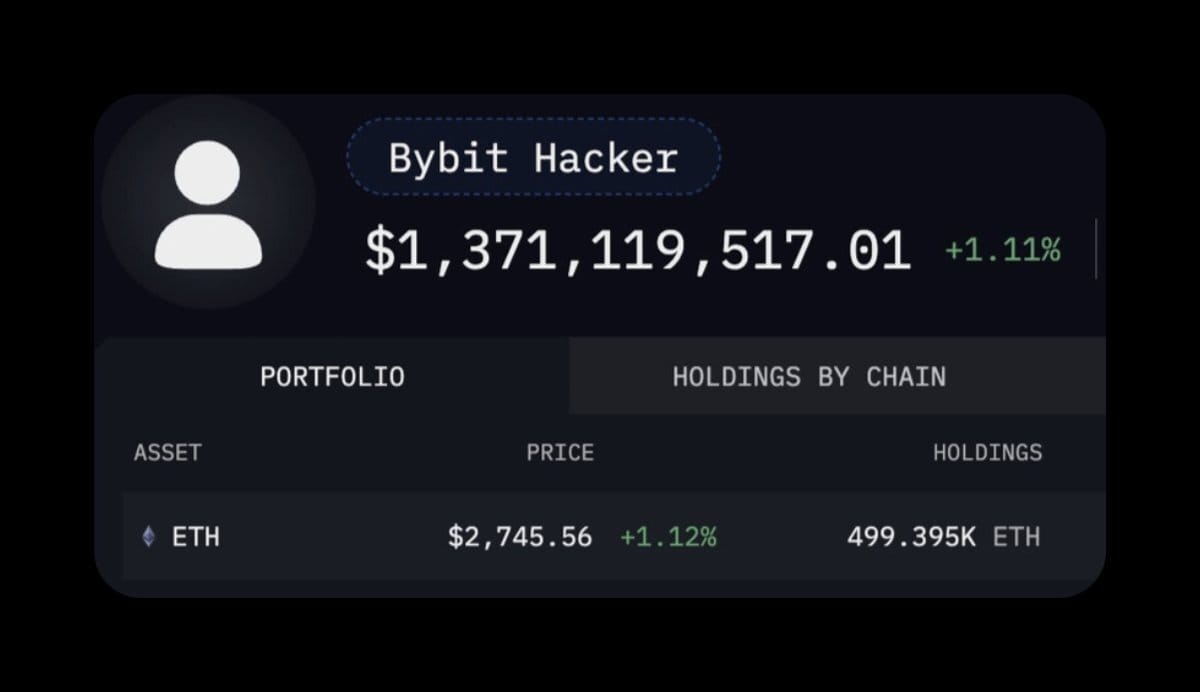
The Heist: A Symphony of Cyber Larceny
On February 21, 2025, Bybit, a prominent cryptocurrency exchange, fell victim to a meticulously orchestrated cyberattack. The perpetrators infiltrated one of Bybit's cold wallets, absconding with over 401,000 Ether, valued at approximately $1.5 billion USD. This incident now stands as the most significant theft in the annals of cryptocurrency history.
Key Details:
Method of Attack: The assailants executed a sophisticated manipulation of the smart contract interface, granting them unauthorized access to Bybit's cold wallet.
Immediate Aftermath: In the wake of the breach, Bybit experienced a surge of over 350,000 withdrawal requests. CEO Ben Zhou assured clients of the platform's solvency, emphasizing that all assets are backed 1:1 and that the exchange remains operational.
The Culprit: Lazarus Group's Digital Fingerprints
While Bybit has refrained from officially naming the attackers, compelling evidence points towards North Korea's infamous Lazarus Group. Blockchain analytics firm TRM Labs has identified substantial overlaps between the addresses used in the Bybit heist and those linked to previous North Korean exploits.
Historical Context:
Previous Exploits: The Lazarus Group's notorious history includes the $600 million Ronin Network hack in March 2022 and the $100 million Harmony bridge theft in June 2022.
Strategic Motive: Isolated by international sanctions, North Korea has systematically targeted cryptocurrency platforms, channeling stolen assets to fund its nuclear and ballistic missile programs.
The Broader Implications: A Wake-Up Call for the Crypto Sphere
This monumental theft transcends the immediate loss of assets; it underscores the systemic vulnerabilities within the cryptocurrency ecosystem.
Industry-Wide Repercussions:
Erosion of Trust: Such high-profile breaches deter potential investors and raise questions about the security frameworks of even the most prominent exchanges.
Regulatory Scrutiny: As these incidents escalate, governments worldwide may impose stringent regulations, challenging the foundational principles of decentralization that the crypto community cherishes.
A Call to Action:
The Bybit heist serves as a stark reminder that in the realm of digital finance, complacency is a luxury we cannot afford. It is imperative for stakeholders to:
Enhance Security Protocols: Implement multi-layered defenses, regular audits, and real-time monitoring to detect and thwart potential threats.
Foster Collaborative Defense: Share threat intelligence across platforms to build a unified front against malicious actors.
Educate the Community: Equip users with knowledge about security best practices, fostering a culture of vigilance and resilience.
In the relentless pursuit of profit and innovation, the cryptocurrency industry must not overlook the ever-present specter of cyber threats. As North Korea's digital marauders continue to exploit these vulnerabilities, the onus is on us to fortify our defenses and safeguard the future of decentralized finance.
📞 Book a Call with the Fraudfather! to fortify your defenses today!
There’s a reason 400,000 professionals read this daily.
Join The AI Report, trusted by 400,000+ professionals at Google, Microsoft, and OpenAI. Get daily insights, tools, and strategies to master practical AI skills that drive results.
Deepfake Love: The Rise of AI-Powered Romance Scams
Fraud isn’t just evolving—it’s adapting in real time. Romance scams have always been a goldmine for cybercriminals, but now they’re being supercharged with deepfake technology, turning deception into an art form. What used to be poorly written texts from a "U.S. Army General" or a "lonely doctor in Dubai" has now become an immersive, AI-driven illusion.
The fraudsters aren’t just catfishing—they’re face-swapping, voice-cloning, and manipulating their targets in real-time. If you thought seeing was believing, welcome to a world where your own eyes betray you.

1. Inside the Deepfake Playbook
This video, uploaded by an online romance fraudster on one of his gang’s Telegram channels, is interesting for several reasons.
🔹 The Fraudster's Face: You can clearly see the scammer’s real identity in the center before the deepfake overlay is applied.
🔹 The Victim's Perspective: On the right side of the video, you see what the victim sees—a fabricated, convincing deepfake of a different person.
🔹 The Fraudster's Intent: The scammer didn’t just upload this video to brag—he’s actively teaching his peers how to pull off the deception.
🔹 Psychological Manipulation: Despite little happening in the conversation, the victim appears delighted, illustrating how easily charm and AI-driven deception work together to build trust.
With just 4GB of RAM and some basic software, the fraudster can swap their face with anyone they choose—movie stars, military officers, or wealthy executives. The result? A real-time, hyper-realistic deepfake that mimics head movements, blinking, and even facial expressions.
One scammer, caught selling this software, even bragged: "It’s so good, you can sip tea, and your deepfake will too."
That’s the level of precision we’re dealing with.
2. The Perfect Con: Why This Works So Well
Romance scams work because they don’t just steal money—they manipulate emotions. The playbook is simple:
💔 Emotional Manipulation – Scammers create urgency, feigning love or distress. Victims feel obligated to "help" their online lover.
📹 The Face-Swap Trust Factor – Video calls used to be a sure-fire way to verify identity. Deepfakes shatter that trust, removing the last layer of protection.
🛑 Low-Tech, High Impact – No need for elaborate social engineering. The scammer just needs a convincing deepfake and a smooth story.

3. How the Setup Works: Virtual Cameras & AI Deepfake Streaming
Deepfake scammers use a virtual camera—a software-based webcam that takes the AI-generated face and feeds it into a live video call.
How it’s done:
Face Swap Software: The fraudster runs deepfake software (like DeepFaceLive) on their PC.
Virtual Webcam: The AI-generated face is fed into OBS Studio or similar software, making it appear as a "real" camera source.
Live Streaming to Video Calls: The virtual cam is used in WhatsApp, Zoom, or FaceTime to project the fake identity in real-time.
Voice Cloning (Optional): Some scammers go further, using AI-generated voices to perfectly match accents and speech patterns.
The entire process is plug-and-play, with tutorials widely available on fraudster forums.
4. How to Fight Back: Defense Strategies
🔹 Deepfake Risk Assessments 📊 – SMBs, financial institutions, and even individuals should adopt deepfake detection protocols.
🔹 Device Fingerprinting 🔍 – Instead of relying on video verification, implement hardware-based authentication to detect anomalies in the user’s device.
🔹 Behavioral Analysis 👀 – AI scams may mimic faces, but human behavior is harder to fake. Look for timing delays, unnatural eye movement, and microexpressions.
🔹 Deepfake Poisoning 🧪 – Use AI adversarial techniques to feed manipulated datasets into detection models, forcing fraudsters to create flawed deepfakes.
🔹 Neural Lags Detection ⚡ – Deepfakes struggle with biological consistency—small asynchronies in blinking, microexpressions, or the delay between facial movements and speech are dead giveaways.
🔹 Reverse Image Searches 🔄 – Many deepfake scammers steal images from social media. Running profile pics through tools like Google Reverse Image Search can expose fake identities.
🔹 Voice-Baiting Techniques 🎤 – Ask deepfake suspects to repeat uncommon words or phrases at random intervals; AI-generated voices often struggle with spontaneous phonetic variance.
🔹 Linguistic Profile Analysis 📝 – Most fraudsters don’t fully mimic speech patterns; analyze grammatical quirks, slang usage, and cultural references that don’t match the identity they present.
🔹 Behavioral Profile Cross-Checking 🔗 – Tie video verification to historical behavior, ensuring scammers can’t just swap faces but must match known social patterns.
💡 Final Thought: The more we rely on digital relationships, the more fraudsters will exploit them. Deepfakes are just the beginning. The real war is against trust itself. The battlefield? Your perception. Stay sharp. Stay skeptical. Stay ahead.
🔥 If you're an SMB owner or fraud analyst, you need to be testing deepfake defenses NOW. Drop me a line ([email protected]) if you've seen cases like this or need help integrating fraud detection tools. 🚨
Intel is only as powerful as the minds that wield it. If this Dead Drop sharpened yours, pass it along—because knowledge hoarded is power wasted. Share it now. 🚀📡
🔍 Think You Can Crack the Code?
Fraudsters manipulate perception. Real analysts spot the truth. Every week, we’ll drop a brain teaser designed to sharpen your pattern recognition, logic, and critical thinking—the same skills that separate fraud victims from fraud fighters.
This week’s challenge is live. Can you solve it?
📲 Text “Pattern” (341) AI-INTEL to get the correct answer.
🔹 Standard message & data rates apply.
🔹 Reply STOP to opt out anytime.
🔹 No spam—just raw intelligence.
Only the sharpest minds will get it right. Are you one of them? 🤔🔥

"Fraud isn’t just about deception—it’s about misdirection. The best analysts don’t see what they expect, they see what’s real. Do you?"
Cognitive Insights

The Architecture of Influence—Where Strategy, Psychology, and Power Collide.
Hacking Charisma: Cognitive Warfare Lessons from the CIA
Influence isn’t about brute force—it’s about understanding the machinery of human thought and pressing the right levers at the right time. The CIA’s case officers don’t just extract secrets; they manipulate perception, craft identities, and orchestrate compliance with the precision of a surgeon.
The most powerful hacks aren’t technical—they’re psychological exploits hidden in plain sight. These are the weapons of persuasion, drawn from the clandestine playbook of espionage, now laid bare for those willing to wield them.
1. 🔄 The Value of a Favor Decays Over Time—Cash Out Quickly
A favor is not an investment—it’s a depreciating asset. The one who grants it sees the act as substantial, recalling their effort and sacrifice. The one who receives it? They appreciate it in the moment, then devalue it with time.
This asymmetry means the most dangerous mistake a favor-giver can make is assuming debt holds value indefinitely. If you’re owed, call in the favor before it loses its weight. If you’re in debt, neutralize it quickly—before its perceived cost balloons in the mind of the giver.
2. 🚪 The “Foot in the Door” Technique—Small Favors Lead to Big Favors
A man who does you a small favor today has unwittingly volunteered himself for larger tasks tomorrow. Why? Because action shapes identity. The moment someone helps you, they subconsciously categorize themselves as "a helpful person."
Want influence? Ask for something small first. A borrowed pen, a minor task, a trivial opinion. Once they comply, their psyche adjusts to accommodate the behavior—and they’ll be primed for larger compliance in the future.
3. 🎭 The Power of Labels—Assign an Identity, and People Will Live Up to It
People hunger for belonging—to be part of something larger, to have a role, a title, a tribe. And when you give them a label, they will do almost anything to live up to it.
Tell a customer they are part of an exclusive group. Tell an employee they are a leader. Tell an audience they are the kind of people who take action. These statements do more than flatter; they embed expectations into their psyche.
The unspoken rule: once people accept a label, they resist behaviors that contradict it.
4. ✍️ Writing Things Down—The Illusion of Commitment
There’s a reason confessions are written. The act of writing isn’t just communication—it’s cementing belief.
Get someone to write something down—a goal, a resolution, a commitment—and you’ve won half the battle. The human mind despises inconsistency; once a statement is written, the subconscious will fight to make it true.
Want customers to stay engaged? Have them list three ways they’ll use your product. Want someone to follow through on a promise? Make them physically write it down. The written word isn’t just ink on paper—it’s a contract with the self.
5. 🧠 The “Because” Hack—The Mind’s Need for Justification
People don’t just make decisions; they rationalize them. And any reason—even a feeble one—significantly increases compliance.
A study found that adding the word "because" to a request—even followed by a completely obvious reason—drastically increased agreement rates.
Example: "Sign up today because spots are limited."
The reason is arbitrary, yet it hijacks the brain’s logic center, making the request feel more rational, more urgent, and harder to decline.
6. 🪞The Mirror Effect—Reflection Breeds Self-Consciousness
The simple act of seeing oneself—whether in a mirror, a reflection, or even a rhetorical question—forces self-awareness. And self-awareness breeds self-judgment.
This is why high-end stores use mirrors near their products. Why gyms line their walls with reflections. Why an innocent-sounding question like “Is your current strategy truly working?” forces a deeper level of introspection.
Want to make people second-guess their decisions? Put a mirror in the room. Want to force someone to confront reality? Make them describe their choices aloud.
The mind’s greatest weakness? Its inability to ignore itself.
Master the Playbook, Master the Game
Espionage is not about brute force—it’s about psychological maneuvering. It’s about knowing which strings to pull, which buttons to push, and how to make someone believe they acted of their own free will.
These aren’t just tactics; they are the architecture of influence. Used wisely, they open doors. Used recklessly, they can unravel the very trust they exploit.
Now, the question remains: do you recognize these strategies being used on you? Or are you already using them yourself?
📞 Book a Call with the Fraudfather! to fortify your defenses today!
About The Fraudfather
The Fraudfather combines a unique blend of experiences as a former Senior Special Agent, Supervisory Intelligence Operations Officer, and now a recovering Digital Identity & Cybersecurity Executive, He has dedicated his professional career to understanding and countering financial and digital threats.
Fast Facts Regarding the Fraudfather:
🌍 Global Adventures: He’s been kidnapped in two different countries—but not kept for more than a day.
🥤 Uncommon Encounter: Former President Bill Clinton made him a protein shake.
🚀 Unusual Transactions: He inadvertently bought and sold a surface-to-air missile system.
⏳ Perpetual Patience: He spent 12 hours in an elevator.
🤝 Unique Conversations: He spoke one-on-one with Pope Francis for five minutes using reasonable Spanish.
🐝 Uncommon Hobbies: He discussed beekeeping with James Hetfield from Metallica.
🏹 Passion for Teaching: He taught teenagers archery in the town center of Kyiv, Ukraine.
✈️ Unlikely Math: Until the age of 26, he had taken off in a plane more times than he had landed.
📞 Book a Call with the Fraudfather! to fortify your defenses today!
This newsletter is for informational purposes only and promotes ethical and legal practices.



