- The Fraudfather's Dead Drop
- Posts
- Your Face Just Robbed You
Your Face Just Robbed You
Eavesdropping on timeless greed in a god-tech age, before your own smile signs the ransom note.


Wiretap Zero: Why We’re Bugging the Underworld
Every week my inbox brims with the same polite accusation:
“Fraudfather, why the obsession with dark psychology? Isn’t technology the real battlefield in fraud and capital?”
Here’s the uncomfortable answer.
Technology mutates at warp-speed; human nature doesn’t budge an inch.
Today’s con artists wield deep-learning GPUs instead of loaded dice, but the pressure points they squeeze e.g.,greed, fear, ego, FOMO - are the same arteries Cleopatra, Ponzi, and Madoff thumbed to death.
Strip away the silicon veneer and every ransomware crew, boiler-room syndicate, and meme-coin puppet master still relies on one timeless variable: our predictable minds.
That’s why Dead Drop Dossier drilled into manipulation first. If you can’t see the strings, the tech is irrelevant; you’re just a marionette waiting to dance.
But enough theory; welcome to Dead Drop Wiretap.
This new alternating Thursday brief is where we eavesdrop on the modern rackets in flagrante delicto, then translate their playbooks into two actionable languages:
Defense: So you never lose a cent to the next synthetic-ID carousel or AI voice clone.
Offense: So you spot the asymmetric upside others miss and build wealth while the herd watches Netflix.
Because make no mistake: fraud fuels fortunes. Criminals milk inefficiencies; savvy operators plug those leaks, or arbitrage them legally. Understanding both sides of the chessboard is how you graduate from pawn to kingmaker.
And it’s global. A bogus Bank of Montreal ad in Toronto, a WeChat scam funnel in Shenzhen, an AI-forged CEO in São Paulo, they all siphon cash through the same borderless pipes.
Currency is just a skin-deep costume; the psychology underneath is universal. If you carry a phone and chase prosperity, your ZIP code offers zero immunity.
So here’s the Fraudfather’s Omertà:
We’ll dissect the freshest cons, deepfakes, social-engineering pretexts, liveness bypasses, step by surgical step.
We’ll weaponize that intelligence into counter-moves and profit angles.
And we’ll do it in a style worth reading.
Failure is no longer an option. It’s a decision.
"We have Paleolithic emotions, medieval institutions, and god-like technology"
Your Face is Now the Smoking Gun.
Let the Heists Begin…
Picture an oak-paneled boardroom at 7 a.m. A junior banker rubs sleep from her eyes as the bank’s CEO appears on the wall with perfect lighting, slight rasp in his voice from the red-eye flight.
“Move the $12 million to the escrow account now, Janet. The Canadians need proof of funds before markets open.”
Janet obeys. The video looked pristine, the cadence unmistakable. Only later, when the real CEO stormed in, alive and un-jet-lagged, did she learn she’d wired the ransom to a ghost. The CEO she saw was a deepfake; the voice was a cloned timbre stitched together by a GPU farm somewhere east of nowhere.
The money? Atomized through crypto tumblers before breakfast.
Welcome to 2025, where your face, and anyone else’s, can be weaponized against you faster than you can say two-factor.
While Janet was draining company coffers, millions of casual scrollers were being lured into a quieter ambush on Instagram. The ads hit Canadian timelines first: jewel-toned banners wearing the livery of Bank of Montreal and EQ Bank, promising “4.5 % guaranteed yield—tap to enroll.” The branding was surgical: right fonts, right color codes, even the legalese was plagiarized line-for-line. Tapping the ad diverted victims to RBCpromos1[.]cfd, a domain only a sociopath could love. It siphoned logins, two-factor tokens, sometimes full passport scans.

Fake EQ Bank ad targeting Canadian banking consumers (Fraudfather) (Bleeping Computer)

A legitimate EQ Bank ad seen on Reddit (Fraudfather) (BleepingComputer)
Malwarebytes analysts later dissected dozens of these promos and found something novel lurking beneath the pixels: short, AI-generated videos of supposed bank reps mouthing sales pitches. Their lips synced perfectly to a cloned voice; but those reps didn’t exist. They were synthetic. Every inflection was baked by GANs (Generative Adversarial Networks), every iris reflection faked. The result? A credibility bomb that detonated inside the limbic system before the prefrontal cortex could raise a single red flag.
Instagram’s algorithm did the rest, optimizing, amplifying, and inserting the scam into feeds of anyone who so much as hovered over the word “savings.”
What is a GAN?: Generative Adversarial Networks (GANs) are the workhorse behind today’s most convincing deepfakes. Think of them as a two-part AI sparring match:
Generator: a neural artist that fabricates images, audio, or video from noise.
Discriminator: a forensic auditor trained on genuine samples, whose job is to catch fakes.
During training, the generator keeps refining its forgeries while the discriminator keeps sharpening its detection skills. They iterate, adversary versus adversary, until the discriminator can no longer tell the generator’s output from authentic footage. At that point, the system can churn out deepfakes that fool both machines and humans alike.
Act II: The Deepfake Dividend
Why does a polished lie work better than a shabby truth? Robert Greene would remind us that humans are wired for appearance; symbols trump substance. Show us the lacquer of authority and we kneel before it, grateful for the chains. Today, AI furnishes that lacquer on demand.
A fresh report making the rounds in fintech back rooms quantified the carnage: deepfake-driven scams consumed nearly 40 % of the $4.6 billion lost to crypto fraud last year. That figure is a punch line delivered by the grim reaper himself. We’re not talking about novelty Tom Cruise parodies; we’re talking organized crime cartels distilling synthetic faces into pure cash flow.
These syndicates don’t need to spearphish anymore; they spear-fabricate, manufacturing entire humans to front their schemes. They open exchange accounts with AI-forged passports, hop on KYC video calls with avatars that blink, breathe, and banter. And because compliance teams still judge liveness by “is the person moving on camera?” the deepfake sails through with a wink.
Act III: The Psychology of a Painless Theft
The Pretexting Funnel - How the Cons Run Recon Before the Kill Shot

The ad doesn’t dump you straight into the fake banker’s lair. First, a slick questionnaire masquerades as mandatory compliance.
The “Eligibility Quiz”
The ad doesn’t dump you straight into the fake banker’s lair. First, a slick questionnaire masquerades as mandatory compliance.“Select your current bank.” (Maps where the money sleeps.)
“Estimate liquid funds you could deposit today.” (Sizes the prize.)
“Pick your risk-tolerance level.” (Signals greed vs. caution.)
Social-Engineering Side Pockets
Mid-quiz, a pop-up chat, fronted by an AI teller avatar, “verifies” your phone number for two-factor security. It’s really harvesting the fastest channel for the follow-up deepfake call. A second prompt grabs your work email “to confirm employer eligibility,” giving the crew workplace context for future spear-phish.Behavioral Fingerprinting
Every click latency, copy-paste, and typo is logged. Smooth typing + corporate email domain = high-value professional. Hesitant scrolling + Hotmail = likely low stakes. The back-end directs high scorers into a priority segment.Trust Escalation Gate
Only after the marks have surrendered data and dopamine does the system unveil the “Senior Investment Officer,” a video deepfake ready to close. Because the victim has already invested effort (commitment bias) and disclosed personal facts (reciprocity pressure), objections vaporize.Handoff to the Fake Banker
Armed with your bank, balance range, employer, and direct line, the avatar greets you by name: “Janet, I see you’ve earmarked $30 K for a no-risk CD. Let’s finalize.” The deal now feels bespoke, inevitable, and safe.
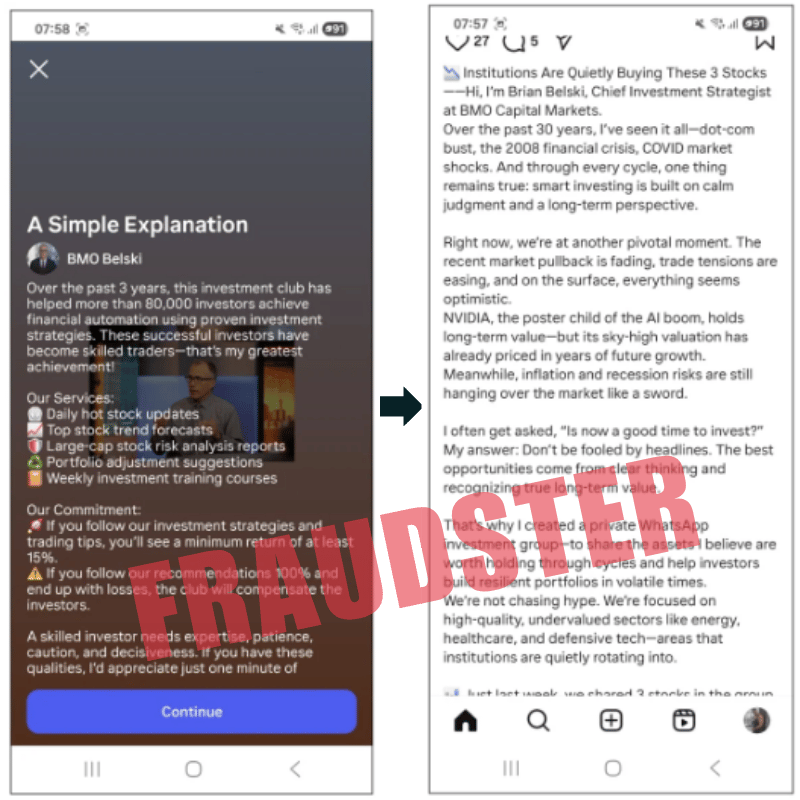
The Handoff to the Fake 'BMO Belski' ads play AI deepfake videos of your “personal” banker. (Fraudfather) (BleepingComputer)
Bottom line: Pretexting isn’t foreplay; it’s reconnaissance. By the time the deepfake appears, the crooks know enough about you to make the con feel like destiny.
Christopher Hitchens once quipped that the essence of mind control is to make obedience feel like freedom. Deepfakes have perfected that art.
Cognitive Ease - The scam flows on rails. Familiar face, authoritative tone, no visual “jank.” Your brain files the interaction under trusted, conserving glucose for later battles.
Commitment & Consistency - Once you nod to a fake authority (“Yes, I want that 4.5 % CD!”) you’ll bend to stay consistent, even if the ask escalates.
Time Scarcity - The synthetic banker warns, “Offer ends today.” Scarcity hijacks the amygdala; deliberation dies.
Social Proof - Fake comment threads under the ad (“Got my bonus in hours!”) reinforce the illusion of a crowd.
By the time you smell the chloroform, your wallet’s in someone else’s pocket.
Act IV: Anatomy of the Clone-and-Confiscate Playbook
Step 1: Harvest the face. Scrape LinkedIn avatars, conference videos, or that heartfelt post about your golden retriever. HD footage preferred, but a 720p Zoom thumbnail will do.
Step 2: Forge the puppet. Feed frames into an open-source face-swap suite. Clone the voice using 30 seconds of interview audio. Cost: $0 if you know the right torrent link.
Step 3: Build the bait. Spin up Instagram ad creatives. Copy a bank’s brand guide-the color codes are public anyway. Train ChatGPT-adjacent models to write ad copy that splits the uprights between “too slick” and “too sloppy.”
Step 4: Relays & Routers. Register a typosquatted domain outside ICANN’s fastest abuse windows (.cfd, .sbs, or a bulletproof vanity TLD). Pipe logs through Tor exit nodes or hacked MikroTik routers in Eastern Europe.
Step 5: Transaction Funnel. Phish credentials, redirect ACH transfers, launder through a cluster of DeFi mixers, exit as privacy coins on an exchange in a jurisdiction where regulators still think “blockchain” is Lego slang.
Elapsed time: 72 minutes from ad approval to first dollar stolen.
Return on investment: 10,000 % or more, because pixels don’t unionize and GPUs never sleep. Build once, scam forever; that’s the cartel calculus.
Build once, scam forever; that’s the cartel calculus in the Generative AI world.
Act V: The Defense Nobody Wants to Pay For
Banks preach “zero trust” but still hinge identity on verifying a face on a screen. That’s like authenticating diamonds with a photocopy. The gap between threat and control widens by the hour.
Why the hesitation?
Cost Aversion - Real liveness analytics (cryptographic challenge-response, biometric depth mapping) costs money today, while the breach is someone else’s headline tomorrow.
Friction Fear - Marketing teams dread any extra click that might tank conversion rates. Better a few extra accounts than a safer pipeline.
Legal Loopholes - In most jurisdictions, liability still waterfalls onto the consumer. If Janet wires $12 million to a thief, the bank may cover pennies on the dollar, but the C-suite rarely bleeds.
Thus the incentive matrix nudges institutions toward the appearance of security—long privacy policies, rotating banners trumpeting “AI Protection!”—rather than ironclad counter-ops.
Act VI: Counter-Moves from the Fraudfather’s Playbook
Kill the Pixel Alone Test
Integrate multi-modal challenges: randomized three-dimensional head turns and a short phrase spoken into the mic. A prerecorded deepfake struggles to match both in sync—today.
Device-DNA & Behavioral Biometrics
Fingerprint browsers and input rhythms. A synthetic account might nail the video but will betray itself with robotic keystroke cadence or a pristine Canvas hash.
Zero-Day Brand Monitoring
Spin up search-engine ads on your own typosquatted domains. Outbid the criminal before he sets the hook. Users landing there get a bright-red warning and an education rather than malware.
Red-Team the Funnel
Run internal ops that impersonate your brand. If your security stack flags them, celebrate; if not, you’ve found the hole before the wolves did.
Criminal Bounties & Public Shaming
A page from the old mafia wars: hang a price tag on verified fraudsters’ heads (legally, of course… cash rewards for intel). Noise attracts hunters; hunters reduce half-life of new schemes.
Act VII: The Moral Fog
Deepfakes tempt more than villains. The marketing intern itching for viral clout, the activist seeking sympathy, the politician desperate for last-minute spin; all will flirt with synthetic media. The line between scam and spin blurs until both wear the same mask.
Hitchens warned that once language is corrupted, thought follows. Deepfakes poison the visual language of trust. If every face can be forged, every testimony becomes suspect. We risk a nihilistic market where skepticism throttles commerce. Business, or democracy, cannot function in total disbelief.
Final Warning from the Wiretap
You’re not paranoid; you’re paying attention. When a screen lights up with the face you trust most, assume the worst and verify backwards. Because somewhere, in a data center that looks more like a casino than a crime den, an algorithm is already practicing your smile, rehearsing your jokes, perfecting the quiver in your voice when you ask your finance team to “please expedite.”
It won’t bother stealing your password. It’ll steal you.
And unless you out-think it now, the next headline won’t be “Instagram Ads Scam Strangers.” It’ll be your name in the subject line of the SEC breach disclosure.
Sleep tight. Keep one eye on the camera… and maybe cover the other with duct tape.
Legal Hustle: This is NOT a fake ad 😏, and a great (and free) read if you are interested in alternative investment strategies.
Get access to the most exclusive offers for private market investors
Looking to invest in real estate, private credit, pre-IPO venture or crypto? AIR Insiders get exclusive offers and perks from leading private market investing tools and platforms, like:
Up to $250 free from Percent
50% off tax and retirement planning from Carry
$50 of free stock from Public
A free subscription to Worth Magazine
$1000 off an annual subscription to DealSheet
and offers from CapitalPad, Groundfloor, Fundrise, Mogul, and more.
Just sign up for our 2-week free trial to experience all the benefits of being an AIR Insider.
Omertà Clause: Share the Wiretap wisely. Use these insights to defend, not defraud, lest you end up starring in our next tape under “perp walk.”
About The Fraudfather
The Fraudfather combines a unique blend of experiences as a former Senior Special Agent, Supervisory Intelligence Operations Officer, and now a recovering Digital Identity & Cybersecurity Executive, He has dedicated his professional career to understanding and countering financial and digital threats.
Fast Facts Regarding the Fraudfather:
Global Adventures: He’s been kidnapped in two different countries—but not kept for more than a day.
Uncommon Encounter: Former U.S. President Bill Clinton made him a protein shake.
Unusual Transactions: He inadvertently bought and sold a surface-to-air missile system.
Perpetual Patience: He spent 12 hours in a pitch-black elevator.
Unique Conversations: He spoke one-on-one with Pope Francis for five minutes using reasonable Spanish.
Uncommon Hobbies: He discussed beekeeping with James Hetfield from Metallica.
Passion for Teaching: He taught teenagers archery in the town center of Kyiv, Ukraine.
Unlikely Math: Until the age of 26, he had taken off in a plane more times than he had landed.
This newsletter is for informational purposes only and promotes ethical and legal practices.


